A Steganography Method for G.729a Speech Coding
通讯作者:
版权声明: 2020 【-逻*辑*与-】#x000a9; 2020 Totem Publisher, Inc. All rights reserved.
展开
Abstract
By analyzing and comparing the G.729a speech coding specifications, this paper proposes an effective information hiding method. The proposed method hides the transmitted confidential information bits according to the need of the hiding information to adjust the last bit value of the excitation pulse position coding in G.729a speech coding, thereby realizing the embedding of secret information. We discussed and introduced in detail the information embedding and extraction algorithm of the proposed information hiding method. In order to test the feasibility and efficiency of the method studied, we conducted simulation experiments. The experiment used six kinds of audio material clips that we recorded, cut and edited by ourselves, namely children's male voice, children's female voice, male singing voice, female singing voice, Chinese classical music, and western music. Experiments show that when the secret information transmission rate is 200 bit/s and the hiding rate is 2.5%, the percentage of PESQ value reduction of the voice carrier proposed by the information hiding method proposed in this paper is 5.31%. While the secret information transmission rate is 300 bit/s and the hiding rate is 3.75%, the percentage of PESQ value reduction is 7.95%. The experimental results showed that the algorithm discussed in this paper has a sound covert communication capacity and strong concealment, indicating that the proposed algorithm demonstrates good information hiding performance.
Keywords:
© 2020 Totem Publisher, Inc. All rights reserved.
1. Introduction
Information hiding is an effective method for the convert transmission of confidential information. It secretly embeds secret information into digital carrier media by using the sensory redundancy of the human senses to the carrier signal, thus hiding the existence of the secret information communication process. Any third parties other than the sender and receiver performing the embedding/extraction behavior are unaware of the existence of this process [1]. The approach of secure and covert information transmission is to embed sensitive information into the ordinary digital carrier media in a way that is not easy to be detected, such as various text, speech, image and audio and video materials. Voice communication is one of the most popular corresponding ways of communication in people's daily life. It owns a very broad application foundation and considerable communication capabilities. Consequently, covert speech communication based on speech codec carrier has a broad application prospect in military, security, commercial and other similar related fields. Study on secret communication of speech coding carrier has crucial scientific research value and application significance. Based on the analysis of the characteristics of G.729a speech coding, this paper studies the algorithms of steganography based on G.729a codebook position adjustment. The simulation results show that: (1) by conducting the information hiding method discussed in this paper, when the capacity of secret information hiding is 2.5% and the transmission rate of secret channel is 200 bit/s, the percentage of PESQ value reduction of the speech carrier is 5.31%; (2) when the secret information hiding capacity increases to 3.75% and the transmission rate of secret channel increases to 300bit/s, the percentage of PESQ value reduced by the information hiding method discussed in this paper is 7.95%; (3) when the capacity of secret information hiding and the transmission rate of secret channel continue to be increased, the percentage of PESQ value reduction of voice carrier is too sharp, which shows that the algorithms has no application value in this occasion. Comparative experiments show that the presented algorithm under this study is improved in terms of privacy and hiding capacity compared with similar algorithms.
The rest of the paper is organized as follows: in Section 2, we introduce related works conducted in related fields. Section 3 studies and analyzes characteristics of G.729a speech codec. We then discuss the proposed information hiding algorithm in Section 4. To evaluate the efficiency and performance of our method and algorithm, we introduce the experimental results and analyses in Section 5. Finally, we summarize our research work in Section 6.
2. Related Work
In the existing speech coding hiding, Li et al. proposed an information hiding method for G.723.1 [2-3], Ma and Wu propose a hiding method for G.721 [4], and Mannell proposed a method for G.723.1 to mine the least significant bit in noise frames for information hiding [5]. Liu [6] proposed a novel approach to embed information during linear predictive coding (LPC) process based on Matrix Embedding (ME). By constructing mapping table to conduct embedding and selection of embedding position according to private key, their approach leads to a better performance with less speech distortion and better security. Paper [7] focused on quantization-index-modulation (QIM) steganography in low-bit-rate speech codec and carried out a novel QIM steganography based on the replacement of quantization index set in linear predictive coding (LPC). Seeing each quantization index set as a point in quantization index space, they embed sensitive information into the above space. Their experiments on ITU-T G.723.1 codec show that their method outperforms the state-of-the-art LPC-based algorithms in the area with respect to both steganographic capacity and steganalysis resistance. In [8], a comprehensive test was carried out for the frame-by-frame bitwise negation of G.729a speech, and it was found that the speech had hidden bits. A method of information hiding combined with matrix coding was proposed. The test results showed that the algorithm has considerable hiding capacity, high embedding rates, and concealment. Huang et al. used inactive speech frames to hide information and integrated the embedding process into coding [9]. Zhang [10] presented a steganographic method by combining F5 and the Simplified Wet Paper Code (SWPC) algorithm. They embedded secret messages in each row of the carrier matrix using the F5 algorithm, while the SWPC algorithm was also used to embed the columns. Their proposed algorithms can obtain better IP speech data steganographic transparency, which outperforms the F5-WPC and SWPC approaches. Yang et al. [11] proposed a steganography scheme using a 3D-Magic matrix to enlarge capacity and improve quality of speech. Theoretical analysis and experiments show that the proposed method can provides sound concealment and the hidden capacity. Paper [12] presented a steganography approach based on text Emotional adjustment based on machine deep learning. By using intelligent dynamic expansion method for text emotional lexicon based on deep learning and conducting matrix encoding algorithm to calculate the minimum modification unit, they effectively improved the privacy, embedding rate, concealment and capacity of sensitive information. In paper [13-14], after counting the less important bits of the compressed G.729 speech coding bit stream, Cao et al proposed an approach to embed sensitive information into the G.729 speech coding stream, and then they designed a voice concealed communication system of IP network by using their proposed algorithm to improve the security of secret information transmission. A steganalysis algorithm based on code-word characteristics statistics, which enables G.729A to carry out QIM steganography to be detected effectively in a short time, was proposed in Reference [15]. Cheng et al. respectively demonstrated the performance of advantages of the two standards in the error concealment process through frame loss measurement and subjective test on G.729.1 and AMR_WB respectively. In their paper, information hiding methods with different capacities are explored for different combinational modulation modes of fixed code book bit in G.729a speech coding. Wu et al. use secure communication based on speech information hiding, they present 2.4Kbps low-bit-rate Mix-excitation linear prediction (MELP) speech into G.729 coding speech and analyze related parameters, and their method can be used in high data embedding capacity hiding systems and can have good effect [16]. Kataoka et al. used G.729 as a component to build a scalable band-split wide band speech coding system that can decode speech from the 16 Kbit/s encoded data. They proposed a pitch prediction scheme to improve quality while retaining scalability to the core coder and proved validity and superiority of their new method through experiments [17].
3. G.729a Speech Coding and Decoding Overview
G.729a is the abbreviated version of the G.729 speech coding specification introduced by ITU (the International Telecommunication Union). It is a standard for speech signal coding of telephone bandwidth. The input analog speech signals are sampled at 8 kHz and quantized by 16 bit linear PCM. The coding principle used is conjugate structure algebraic code excited linear prediction (CS-ACELP). CS-ACELP is based on the principle of the code excited linear prediction (CELP) coding mode. 80 sample points comprise a speech frame. Speech signals are analyzed, parameters (linear predictive filter coefficients, residual signal processing, the serial number of adaptive code book and fixed code book, pitch analysis, adaptive code vector gain, and fixed code vector gain) are extracted, and these parameters are encoded and packaged for sending [18-19]. The allocation of 80 bits of the G.729a parameter coding is as shown in Table 1 [20]. At the decoding end, the received bit stream is restored to parameter coding, and each parameter is obtained after decoding. The adaptive code vector is obtained from the adaptive code book by using the adaptive code vector sequence number, the fixed code vector is obtained from the fixed code book by using the fixed code vector sequence number, and they are multiplied by their gain and then added by points to form the excitation sequence. The synthetic filter is composed of linear predictive filter coefficients. The so-called adaptive code book method is used to realize long-term or pitch synthesis filtering. After calculating the synthetic speech, the post-filter is used to further improve the quality of the original voice.
Table 1 G.729 CS-ACELP coding frame bit allocation
| Parameters | Codeword | Bits number per frame |
|---|---|---|
| LSF | L0, L1, L2, L3 | 18 |
| Adaptive-codebook delay index | P1, P2 | 13 (8+5) |
| Pitch-delay parity index bit | P0 | 1 |
| Fixed-codebook index | C1, C2 | 26 (13+13) |
| Fixed-codebook sign index | S1, S2 | 8 (4+4) |
| Codebook gains (stage 1) | GA1, GA2 | 6 (3+3) |
| Codebook gains (stage 2) | GB1, GB2 | 8 (4+4) |
| Total | 80 |
4. Information Hiding and Extraction Algorithm
4.1. Information Hiding Algorithm
The fixed-codebook of G.729a encoding is a conjugate algebraic structure codebook. Each fixed-codebook vector consists of four non-zero excitation pulse signals, and each excitation owns the amplitude sign of either +1 or -1. The location indexes of G.729a fixed-codebook speech encoding frame consists of four excitation pulses, which are named as
Table 2 The forty indexes' position allocation structure of the four excitation pulses in G729a Fixed-codebook
| Number of pulse | Amplitude sign | Excitation pulse location index | |
|---|---|---|---|
| Sub-frame 1 | i0 | +1/-1 | 0, 5, 10, 15, 20, 25, 30, 35 |
| i1 | +1/-1 | 1, 6, 11, 16, 21, 26, 31, 36 | |
| Sub-frame 2 | i2 | +1/-1 | 2, 7, 12, 17, 22, 27, 32, 37 |
| i3 | +1/-1 | 3, 8, 13, 18, 23, 28, 33, 38 4, 9, 14, 19, 24, 29, 34, 39 |
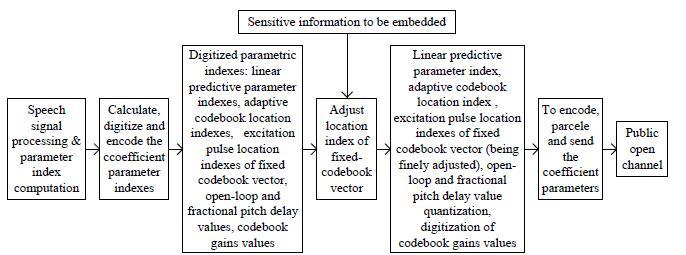
The detail flow chart of the sensitive information conceal procedure of the proposed steganography method in G.729a speech codec by adjusting the location of the excitation pulses is as shown in Figure 1.
The proposed steganography algorithm based on adjustment of codebook indexes of G.729a speech coding is as follows:
Step 1 Obtain G.729a speech frames of 80 samples per second, analyze and extract the excitation pulse indexes of four fixed codebooks in the speech frames. After the above analysis, we can find out that the first, second and third pulses are all 3 bits. Because the fourth pulse is divided into odd and even groups, it is represented by 4 bits.
Step 2 Fetch the confidential information to be embedded, and digitize the information into a binary string consisting of 0 or 1.
Step 3 According to the current value of the information bit to be hidden (ie. 0 or 1), select the index number of the pulse to be embedded with sensitive information. If the parity of the index number and the information value to be hidden is not the same, adjust the lowest order of the pulse index number to make it the same as the parity of the information value to be hidden; if the parity of the index number and the information value to be hidden is the same, do not adjust the pulse index number because the information to be hidden has been embedded accordingly.
Step 4 If the secret information that needs to be hidden has not been completely embedded, go to Step 1.
Step 5 End.
4.2. Information Extraction Algorithm
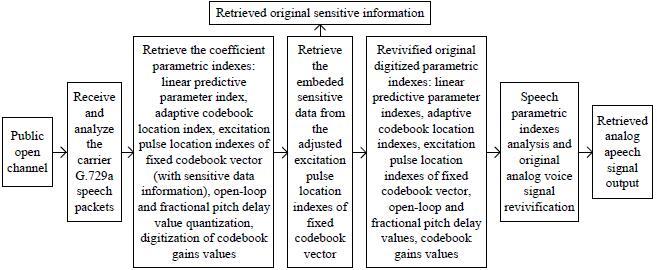
The method of extracting sensitive information is opposite to the embedding process. The specific process is: receive the voice data packets transmitted from the open public channel and call G.729A decoder to extract the excitation pulse index of the fixed codebook in G.729A speech coding. The hidden confidential information can be extracted according to the parity property of the index number value of the excitation pulse. The detailed flow chart of the confidential information extraction algorithm studied in this paper is as shown in Figure 2.
The proposed confidential information extraction algorithm is as follows:
Step 1 Fetch and analyze the carrier G.729a speech coding packet, and extract the coefficient parametric indexes.
Step 2 Pick out the excitation pulse location indexes of the fixed codebook vector (i.e. with sensitive confidential information), and then retrieve the embedded confidential information according to the parity of the excitation pulse location indexes' value.
Step 3 If the secret confidential information is not retrieved completely, go to Step 1.
Step 4 End.
5. Experiment and Results
5.1. Experiments on Selection of Modulation Schema of Pulse Position of G.729a Code Book for the Algorithm
As mentioned above, in order to embed confidential information into the G.729a speech carrier, the excitation pulse position should be adjusted according to the sensitive information that is to be embedded. That is, the excitation pulse position should be added by 1, subtracted by 1, or randomly added/subtracted by 1 according to the confidential information to be embedded. In order to test the influence of the above three processing tactics on the carrier speech coding, we take the first pulse location index of G.729a coding as our experimental example of this stage. In the experiment scenario of embedding sensitive information into the first pulse location index of G.729a coding, and according to the parity of the secret information to be embedded, the embedding of confidential information is achieved by adding 1, subtracting 1, and randomly adding and subtracting 1, respectively. The objective Perceptual Evaluation of Speech Quality (PESQ) test is performed by using the audio material fragments set containing six kinds of voices that we recorded, cut or edited by ourselves. The six kinds of voices being used are: boy's voice, girl's voice, male singing voice, female singing voice, Chinese classical music, and western music. In our voice clip library, we collected 200 pieces of each kind of the above six voices. We use the aforementioned speech fragments library edited by ourselves to observe the effect of information hiding by using the percentage of the PESQ score with confidential information over the PESQ score without confidential information. The results of experiments are as shown in Table 3.
Table 3 The PESQ score and its percentage under different hiding processing scenarios of fixed codebook index adjustment
| Experiment condition | boy voice | girl voice | male singing | female singing | Chinese music | western music |
|---|---|---|---|---|---|---|
| No confidential information embedded | 2.841425 | 2.962733 | 3.287391 | 2.910467 | 2.876323 | 2.917364 |
| Information hiding of code book bit +1 processing | 2.696228 | 2.803634 | 3.096394 | 2.762906 | 2.726467 | 2.752533 |
| 94.89% | 94.63% | 94.19% | 94.93% | 94.79% | 94.35% | |
| Information hiding of code book bit -1 processing | 2.683726 | 2.792376 | 3.111844 | 2.749518 | 2.718988 | 2.770621 |
| 94.45% | 94.25% | 94.66% | 94.47% | 94.53% | 94.97% | |
| Information hiding of code book bit randomly +-1 processing | 2.691682 | 2.810745 | 3.109543 | 2.764071 | 2.719851 | 2.776164 |
| 94.73% | 94.87% | 94.59% | 94.97% | 94.56% | 95.16% |
In Table 3, the data of the first row is the average PESQ values when no information is being embedded into the speech, while the data in other rows are the average PESQ values when confidential information has been embedded. From Table 3, we can see that the difference of the change reduction percentage of PESQ score of the carrier speech is not obvious when the strategy of adding 1, subtracting 1, or randomly adding/subtracting 1 is used for information hiding. In other words, the effect of the reduction percentage of PESQ value on the G729a coded voice when hiding information under the above steganography scenarios is almost the same.
On the other hand, in order to test the effect of hiding information by modifying the parity of the lowest bit of G.729a gain coding, we also carry out the experiment of adding 1 and subtracting 1. The results of experiments using four types of speech, also edited by ourselves, are shown in Table 4.
Table 4 The PESQ score and its percentage under different hiding processing scenarios of gain coding adjustment
| Experiment condition | boy voice | girl voice | male singing | female singing | Chinese music | western music |
|---|---|---|---|---|---|---|
| No confidential information embedded | 2.841425 | 2.962733 | 3.287391 | 2.910467 | 2.876323 | 2.917364 |
| Information hiding of gain bit +1 processing | 1.974506 | 1.888446 | 2.151926 | 1.921781 | 2.049955 | 2.111880 |
| 69.49% | 63.74% | 65.46% | 66.03% | 71.27% | 72.39% | |
| Information hiding of gain bit -1 processing | 2.112599 | 2.010807 | 2.292298 | 2.086514 | 2.089073 | 2.152723 |
| 74.35% | 67.87% | 69.73% | 71.69% | 72.63% | 73.79% |
Again, in Table 4, the data of the first row is the average PESQ values when no information is being embedded into the speech, while the data in other rows are the average PESQ values when confidential information has been embedded. As can be seen from Table 4, using the modification of the lowest bit of gain coding to hide information has an obvious negative effect on the speech carrier, so it is impracticable for steganography of sensitive information.
5.2. Experiments of Information Hiding under Different Embedding Capacity
Next, we conduct experiments to observe reduction percentage of PESQ score of the G.729a carrier speech so as to test the quality of the studied steganography algorithm. The experimental audio fragments set used here is as the same as Section 5.1. We do the experiment on the following five scenarios: (1) use all the fourth excitation pulse location indexes of the two sub-frames to embed sensitive information; (2) use all the fourth excitation pulse location indexes of the two sub-frames plus the third one of the first sub-frame to embed sensitive information; (3) use all the fourth excitation pulse location indexes of the two sub-frames plus the third one of the second sub-frame to embed sensitive information; (4) use all the fourth and the third excitation pulse location indexes of the two sub-frames to embed sensitive information; (5) use all the fourth, the third and the second excitation pulse location indexes of the two sub-frames to embed sensitive information. The average degradation percentages of PESQ values before and after steganography are determined by using the presented algorithm, as shown in Table 5.
Table 5 The degradation of average PESQ scores before and after steganography is conducted
| Experiment condition | boy voice | girl voice | male singing | female singing | Chinese music | western music | average |
|---|---|---|---|---|---|---|---|
| No confidential information embedded | 2.841425 | 2.962733 | 3.287391 | 2.910467 | 2.876323 | 2.917364 | 2.965951 |
| Experiment scenario (1) | 2.679748 | 2.807782 | 3.112173 | 2.757085 | 2.724453 | 2.769454 | 2.808447 |
| 94.31% | 94.77% | 94.67% | 94.73% | 94.72% | 94.93% | 94.69% | |
| Experiment scenario (2) | 2.600756 | 2.724529 | 3.016839 | 2.686652 | 2.648231 | 2.700604 | 2.729602 |
| 91.53% | 91.96% | 91.77% | 92.31% | 92.07% | 92.57% | 92.04% | |
| Experiment scenario (3) | 2.598483 | 2.719493 | 3.028673 | 2.687234 | 2.649956 | 2.699437 | 2.730546 |
| 91.45% | 91.79% | 92.13% | 92.33% | 92.13% | 92.53% | 92.06% | |
| Experiment scenario (4) | 2.341050 | 2.453439 | 2.743985 | 2.466621 | 2.414961 | 2.463714 | 2.480628 |
| 82.39% | 82.81% | 83.47% | 84.75% | 83.96% | 84.45% | 83.64% | |
| Experiment scenario (5) | 2.141582 | 2.250492 | 2.453051 | 2.180813 | 2.149189 | 2.212237 | 2.231227 |
| 75.37% | 75.96% | 74.62% | 74.93% | 74.72% | 75.83% | 75.24% |
Similarly, the data in the first row in Table 5 is similar to that in Section 5.1 and 5.2. From Table 5, we can see that when using just the fourth excitation pulse location indexes to embed sensitive information, where the sensitive information transmission speed is 200bits/s, the average decreased percentage of PESQ values is 5.31%. With the embedding rates going up, the average decreased percentage of PESQ values also goes up. In particular, when the fifth scenario is used, the percentage of PESQ value reduction reaches nearly to 25%, indicating that this situation is no longer applicable for information hiding.
5.3. Comparative Experiment Results Between our Algorithm and Similar Algorithm
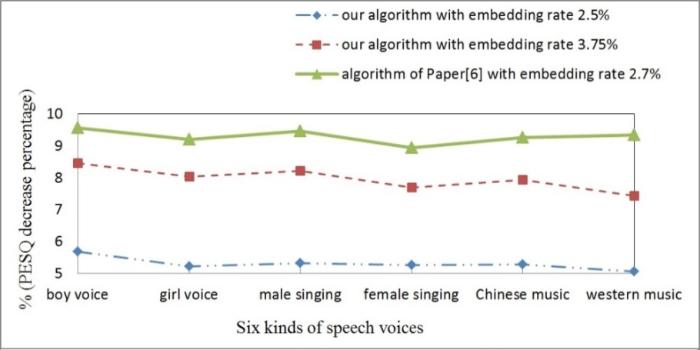
To further test the steganographic performance and efficiency of our algorithm in depth, we compare the algorithm studied here with the approach presented in Literature [8], which is very similar to our algorithm. The experiments are carried out by using the same audio material fragments library described in Section 5.1. For convenient and accurate comparison, we do the comparative experiments under the approximate similar embedding rate. The comparative experiment results of the PESQ score value reduction percentage of the proposed algorithm and that of Literature [8] are shown in Figure 3.
As shown in Figure 3, the average decrease percentage of PESQ value of the studied steganography method is smaller than that of Literature [8], which tell us that the confidentiality, concealment, imperceptibility and total performance of the approach studied here are better than Literature [8].
We would also like to further compare the embedding rate and the related decrease percentage of PESQ value between the algorithm presented here and that of Paper [8]. As mentioned in [8], the average embedding rate was 2.678, and the best PESQ score reduction percentage was more than 9.5%. From Table 5, when 3 bits are embedded into the carrier G.729a speech, we can see that the embedding rate of the algorithm studied is 3.75, while the PESQ score reduction percentage is less than 7.95%. This experimental result shows that the proposed algorithm achieves more sound performance and concealment than that of reference [8].
Figure 3. PESQ score reduction percentage of our algorithm and similar algorithm in [8]
6. Conclusion and Future Work
The G729a speech codec uses 8000 Hz to sample the original analog speech signal encoded, so that each frame has 80 samples. Thus, there are 100 frames of speech signal per second. The PESQ score of G729a speech coding at an 8kb/s compression coding rate is 3.6. The overall case of four types of speech, the information hiding capacity per second, and the percentage of the corresponding PESQ scores compared with the PESQ scores without hiding information are shown in Table 6.
Table 6 G.729a encoding hidden effects per second
| Hidden quantity | Hiding rate | PESQ average percentage | PESQ reduction percentage |
|---|---|---|---|
| 200 bits per second | 2.5% | 94.69% | 5.31% |
| 300 bits per second | 3.75% | 92.05% | 7.95% |
| 400 bits per second | 5% | 83.64% | 16.36% |
| 500 bits per second | 10% | 75.24% | 24.76% |
As shown in Table 6, when only the fourth pulse of the subframe is used to hide information, that is, 2 bits of information are hidden per frame, 200 bits of information can be hidden in one second. The PESQ score ratio of the voice is 94.69%. When the third and fourth pulses indexes of the subframe are used to hide the information, that is, 2, 3, or 4 bits of information are hidden per frame, 300 bits, 400 bits and 500 bits of information can be hidden per second, the PESQ score ratios of the voice are 92.05%, 83.64% and 75.24%, respectively. These results tell us, when the embedding rate goes up too high (for example, more than 400 bits/s), the decrease in percentage of PESQ score goes up sharply and thus the scenario is not applicable for steganography sensitive information. To summarize, the experimental results show, when the embedding rate of confidential information is rational, the information hiding method studied in this paper has less negative effect on the quality of the carrier speech, and the effect of information hiding is acceptable, showing that proposed algorithm demonstrates good information hiding performance.
In the future, we will further study and explore the robustness and reliability in practical applications. In addition, the use of other corresponding parameters' information approach of other carrier speech coding to achieve information hiding is also a direction for our further exploration.
12.F. F. Li, H. Tang, Y. K. Zou, Y. F. Huang, Y. Y. Feng, and L. X. Peng, “Research on Information Security in Text Emotional Steganography based on Machine Learning,” Enterprise Information Systems, 2020, (Early access, Published online: 11 Feb 2020, DOI: 10.1080/17517575.2020.1720827)
13.Y. F. Huang, C. H. Liu, S. Y. Tang, and S. Bai, “Steganography Integration into a Low-Bit Rate Speech Codec,” IEEE Transactions on Information Forensics and Security, Vol. 7, No. 6, pp. 1865-1875, November 2012
14.Y. Q. Cao, S. Bai, K. Cai, and W. D. Li, “Study on Convert Communication System based on G.729compressed Voice Stream,” Modern Electronics Technique, Vol. 36, No. 17, pp. 68-70, September 2013
15.S. B. Li, D. H. Sun, J. Yuan, and Y. F. Huang, “A Steganalysis Method for G.729A Compressed Speech Stream based on Codeword Distribution Characteristics,” Tien Tzu Hsueh Pao/Acta Electronica Sinica, Vol. 40, No. 4, pp. 842-846, April 2012
16.Z. J. Wu, H. Cao , and D. Li, “An Approach of Steganography in G.729 Bitstream based on Matrix Coding and Interleaving,” Chinese Journal of Electronics, Vol. 24, No. 1, pp. 157-165, 2015
17.A. Kataoka and S. Hayashi, “Scalable Wideband Speech Coding using G.729 as a Component,” Systems and Computers in Japan, Vol. 36, No. 3, pp. 65-74, 2005
18.H. F. Cheng, Y. H. Yang, R. M. Hu, and S. Wang, “Research of Error Concealment and Control based on G.729.1 and AMR_WB,” Audio Engineering, Vol. 2011, No. 12, pp. 68-72, December 2011 (in Chinese)
19.X. H. He and Y. F. Huang, “Implementation of ITU-T G.729.A Low Rate Speech Codec,” Communications Technology, Vol. 2002, No. 2, pp.1-3+6, March 2002
20.“ITU-T Recommendation of Coding of Speech at 8 kbit/s using Conjugate-Structure Algebraic-Code-Excited Linear Prediction (CS-ACELP),” (http://www.itu.int/rec/T-REC-G.729-201206-I/en, June, 2012)
The authors have declared that no competing interests exist.
参考文献
| [1.] |
Gu and X. L. Cao, “Research on Information Hiding Technology,” in
|
| [2.] |
Wang and D. F. Ma, “Information Hiding based on Real-Time Voice in DCT Domain,” Computer Engineering and Design, Vol. 22, No .
|
| [3.] |
“A Steganographic Method based on High Bit Rates Speech Codec of G.723.1,” in
|
| [4.] |
“Approach to Hiding Secret Speech Information in G.721 Scheme,” in
|
| [5.] |
|
| [6.] |
|
| [7.] |
|
| [8.] |
Guo and H. Tian, “An Information Hiding Method based on G.729a Speech,” Journal of Huaqiao University (Natural Science), Vol. 35, No .
|
| [9.] |
“Steganography in Inactive Frames of VoIP Streams Encoded by Source Codec,” IEEE Transactions on Information Forensics and Security, Vol. 6, No .
|
| [10.] |
|
| [11.] |
|

/
| 〈 |
|
〉 |